Hello friends! There are many resources on the Internet where victims of fraudsters talk about the theft of funds from plastic cards. Everyone has a mobile phone, Internet banking is linked to many cards by default. Clients, in fact, don’t mind, because this is the most convenient way to pay for goods and services without leaving home. A code from SMS is used to protect payments. But to what extent is such protection justified? Let's talk today about how scammers withdraw money through mobile banking. Go…
Remote banking has its advantages and disadvantages. Some people are simply afraid to pay with a bank card, some are intensively studying information about ways to protect themselves from fraudulent schemes. The most popular query according to statistics is “money was withdrawn from a Sberbank card via mobile banking: how to return the money?” Let's talk about safety rules in more detail.
Vulnerabilities in online resource protection
Fraudsters take advantage of flaws in the banking system to withdraw money from other people's accounts. Consumers often act recklessly, which plays into the hands of criminals. Statistics show: the annual amount of stolen money from card accounts is about 1 billion rubles. At the same time, the Central Bank records at least 400-420,000 cases of theft every year.
The facts are that fraud with bank cards through mobile banking today occurs more often than banal pickpocketing, which was so rampant 10 years ago. More than 23% of transactions in 2020 and 2020 were marked as suspicious and were blocked by banks at the stage of entering information from plastic cards or at the time of identification.
The most vulnerable points in the protection of online resources, and therefore in the protection of clients who actively use their services, are the leakage of personal and payment information. The threat of cyber attacks is partially reduced due to the implementation of multi-level confirmation systems and the latest IT security solutions. But this is by no means a panacea.
About 80% of information leaks occur due to the negligence of employees of the same online resources. A carelessly opened email launches viruses onto servers and steals all information in a matter of hours.
Bank data warehouses are regularly subject to cyber attacks. Last year, every fourth bank in the world was subject to a DDoS attack, with the average damage from manipulation amounting to approximately $1.1 million per bank.
Your own smartphone poses no less a threat. With its help, attackers open personal accounts, even if physical control over the device has not been lost. You may not even suspect that your phone already has a program for reading data and passwords; all you have to do is receive an SMS with the code.
How scammers find out bank card numbers: 5 main ways
What schemes do scammers use to withdraw money from other people’s bank cards? Basically, scammers use the following methods:
- Skimming.

Science and technology are developing by leaps and bounds. Criminals are not far behind. They obtain information about the cards of their victims by introducing special devices into ATMs. When a person makes a transaction through an ATM, the device reads the data. Having taken possession of them, fraudsters create a duplicate card and can easily withdraw all funds from the account using it. To avoid becoming a victim of skimming, you need to withdraw money from ATMs installed in high-traffic areas. The constant presence of people does not give crooks the opportunity to install a reading device.
- Phishing. Phishing is an English word that means fishing. This method of fraud involves redirecting victims to fake websites of banks of which they are clients. After entering your login and password to enter your personal account, criminals take possession of them and sometimes even send a message on behalf of the bank asking for a CVV or PIN code. There are other ways to steal information. Only exceptional care and suspicion will help you avoid falling for the trick. We must not forget that even bank employees do not have the right to request CVV and PIN codes, and therefore a request for this information clearly indicates fraudulent activity.
- Scheme with purchase/sale advertisements.
This scheme works like this: the swindler calls the seller at the number specified in the ad and says he wants to buy the product. At the same time, he is in a great hurry to complete the transaction as quickly as possible and asks where to transfer the payment. Having received the bank card number, the fraudster tries to find out its expiration date (for example, casually asking if it has expired) and the three-digit CVV code (usually asked for, stating that the payment did not go through, etc.). It happens that the seller is asked for a confirmation code from an SMS from the bank sent to his phone. All this should be alarming. No information can be passed on to strangers, since money can only be transferred using the card number. Other data gives thieves access to the victim’s money.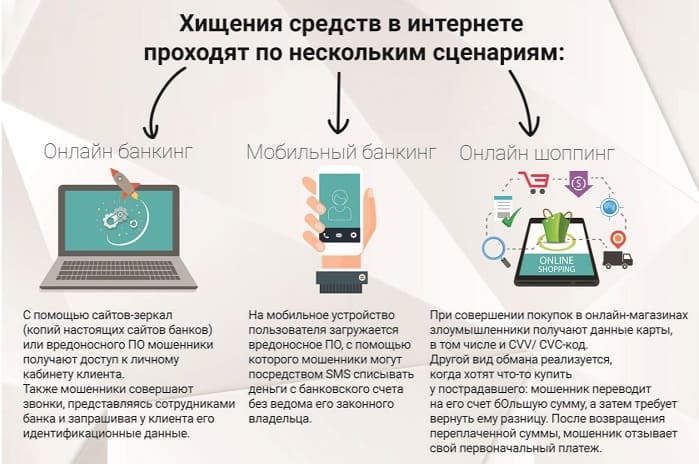
- Payment for purchases, transfer of money on websites. Fraudsters have long been creating fakes of popular Internet sites.
Their URL differs only slightly from the original one, so users often do not notice the catch and enter the details of their bank cards. The data is immediately captured by attackers. They also send fake messages to their potential victims stating that their credentials need to be updated, indicating the address of a clone site. If you do not suspect fraud and follow all the instructions, then the information on the card (and then the money) ends up in the hands of the criminals. Those who like easy money can call bank clients and introduce themselves as their employees, asking for certain data. You must always be on your guard - bank clerks never ask for confidential information. If you are asked for the three-digit code indicated on the back of the card, or a code word, this is definitely a scam. You need to be careful, even if you know for sure that you are on a page on the original site. For example, scammers often operate on the above-mentioned Avito. They introduce themselves as buyers, state that they have difficulties transferring payment for the goods, and ask for additional information. In such cases, you should stop all contact with them, and also pay attention to suspicious calls and SMS. - Manipulating the phone.
Recently, in order to steal funds, criminals often implement the following scheme: they persistently call their victims several times and say that they dialed the wrong number, or they are completely silent for a while and disconnect. At the same time, they do not ask for a bank card number; they recognize it in a different way. What they are interested in is the victim’s SIM card. If, after making calls, your phone account is replenished with a small amount, this is a cause for concern. After the replenishment, the attackers contact the Network operator and report the loss of the SIM card. At the same time, they provide data on the latest incoming calls, the date and amount of the last credit to the account. The operator provides them with a new SIM card and blocks the “lost” one. The rightful owner of the number remains without contact until he finds out what happened. During this time, the scammers manage to “clean up” the victim’s accounts.
Rules for safe use of mobile banking
The agreement with Sberbank lists the requirements that guarantee the safety of remote customer service. A separate chapter is devoted to the use of plastic cards. Failure to comply with the points leads to refusal of assistance and return of the stolen money.
At a minimum, the client must:
- store the information carrier in a place inaccessible to strangers, preferably separately from the owner’s identification documents and money;
- monitor the actions of officials - cashiers, sales managers, service workers - with the card;
- remember PIN - it is prohibited to write down and tell strangers the code.
SMS notifications become an additional means of protection. Some clients deliberately save on this service, not suspecting that losses from such negligence can be much significant. For example, an unscrupulous cashier passes the card through the reader several times, and the bank writes off a double amount. You can instantly notice such manipulation only through a received SMS; you don’t check your account balance after every purchase in the supermarket.

Also, financial institutions do not recommend logging into mobile banking when using open Internet networks. You connect to an open access point, such as a supermarket or shopping center, and simply make your phone visible to intruders.
A separate security item includes responding to SMS with spam content - “you won 100,000 rubles, follow the link” or “your card is blocked, urgently call the number...”. Such SMS, as well as phishing emails, launch viruses into your phone. And as soon as you log into your mobile bank, the malware reads confidential information or simply writes off all the money from your cards.
How to protect yourself from scammers
To protect your finances from criminals, keep the following in mind:
- When making purchases on the Internet, carefully monitor the line in the browser - it should not change; if this happens, you should immediately refuse the purchase, as you may be redirected to a phishing site where all card data is counted.
- Do not store passwords in SMS or notes.
- Set up alerts from your bank about money withdrawals.
- If you don't use your card often, check your transaction list regularly.
- Do not download unverified programs to your phone.
- When changing a SIM card, be sure to check whether any confidential information remains on it.
- If you suspect that someone has accessed your data, immediately go to the bank and block your card.
Fraud regarding finances is punishable by law on the basis of Article 159.3 of the Criminal Code. For this crime, the fraudster faces a fine, arrest, correctional labor, and even restriction of freedom. In addition, he will have to reimburse all stolen funds to the owner.
Types of fraud through mobile banking
Despite the improvements, payment transactions using a plastic card and smartphone are at increased risk. To avoid becoming a victim of circumstances, we recommend that you constantly remember the methods of attackers.
The most common ways to gain access to an account include:
- telephone card fraud;
- phishing;
- malicious use of an ATM.

In almost every method, criminals rely on the human factor - fear, confusion, slow reaction to what is happening. Without your help, many thefts would not have happened a priori. You've probably heard that an experienced thief only needs a couple of minutes to hack an anti-theft system, but a “stealer” of your money from your account needs to do it in 30 seconds - before your brain issues a warning about the danger 

Phone scam and vishing
What is vishing?
Vishing (English abbreviation vishing / from voice phishing) is psychological manipulation, the purpose of which is to force the victim to voluntarily provide personal and payment information on the card.
The most popular technique used by criminals is to inform the cardholder that funds in the account have been blocked. This could be sending messages (SMS, MMS) or calling, the main thing is surprise, a quick text, more smart words and repetition of the phrases “your money is blocked”, “you are under financial control monitoring”, “you have 4 minutes to unblock” and etc. depends on a situation.
The interlocutor introduces himself as a security officer, a controller of financial transactions, an inspector of the financial monitoring department, and offers an instant solution to the problem - provide the login code, information from the front and back of the plastic card.
The first sign that they are trying to deceive you is haste. You are not given a second to think about what is going on. They do not answer your questions about who blocked your money and why; you are not offered to contact the bank, go to the branch, or call the hotline. All that is required here and now:
- a 16-character number on the front of the card;
- validity period in XX/XX format;
- CVV code on the back of the card.
The best thing to do is to drop the call and redial the bank's hotline number yourself. It is on every card, so it is always at hand. What other actions will not hurt:
- Check the caller's number through a Google search, since modern tracking systems store thousands of suspicious callers and particularly active telephone scammers.
- Consult with your bank about additional protection for your accounts. You are already in the attackers' database, and hacking attempts may be repeated.
- Check the limits for cash withdrawals, online transfers and payment for goods/services on the Internet for all your cards. Raising the limit is a matter of 5 minutes, but you will definitely block scammers’ access to remote withdrawals.
Very rarely, but it happens that the caller begins the dialogue by voicing your card number. That is, in some way he has already obtained 16 digits, for example, photographed in a public place or in a store. Then be sure to reissue the card. The account number will remain the same, but the payment details will change.
Precautionary measures
Unfortunately, it is known that they can withdraw money from a phone account if it is infected with a virus. There are no claims against the cellular service provider. If the phone has been infected with a virus, resulting in a charge, the only thing that can be done is to contact a cell phone repair center to remove the virus. However, there is no talk of getting the money back. To avoid such situations in the future, it is advisable to install a reliable anti-virus program on your mobile phone.
Phishing scheme
This type of money theft, as we mentioned above, is associated with the installation of malware on computers and mobile devices. We often download various applications from the network: for games, communication in communities, searching for videos, books, pictures. And as always, we try to save money and find free versions. Such savings lead us to untested resources. After a reboot, malicious software penetrates the smartphone’s control system.
The danger of phishing is as follows:
- instant transfer of all payment data and one-time code to attackers via the Internet;
- blocking messages about the movement of funds on the client’s account - you may not even know that you were robbed.
The program may not reveal itself right away.
For example, the settings will track the receipt of large amounts into your account. Waiting for the right opportunity, the program can quietly remain in the system for months. This is why you regularly receive notifications on your smartphone about the need to update the operating system. Along with updates, developers launch antivirus programs, cleaning your phone of all extraneous codes.
For example, like this:
ATM as a tool for illegal enrichment
As the report of the Central Bank of the Russian Federation shows, more than 200 thousand ATM software systems have been installed in Russia. Of course, most of them are located in bank branches, in crowded stores, and shopping centers. However, some ATMs are forced to be located in remote areas, on sparsely populated streets, where there is insufficient lighting and no traffic at night. Criminals take advantage of this and illegally install reading devices on external ATM panels.
The peculiarity of such designs is that they are difficult to notice; the appearance of the ATM is no different.
Mechanical means include devices:
- skimmers - devices for reading data from a magnetic stripe;
- panel overlays with buttons, they are called a pin pad;
- video cameras to record the PIN code.
All these covers are installed hastily and are not particularly secured, because they also need to be removed quickly, without attracting attention. Before using the ATM, don’t be too lazy to pick at the code entry panel; the false panel comes off easily; pick at the plastic cover on the panel that dispenses banknotes - it’s installed so that the money gets stuck and you can’t withdraw it.
But we are interested in another type of fraud, when you are asked to come to an ATM and, under dictation, solve your certain “problem” with the card. You can call this situation an advanced type of vishing, because actually getting a person to voluntarily perform so many manipulations is already a skill.
Here is a real story from a banking forum:
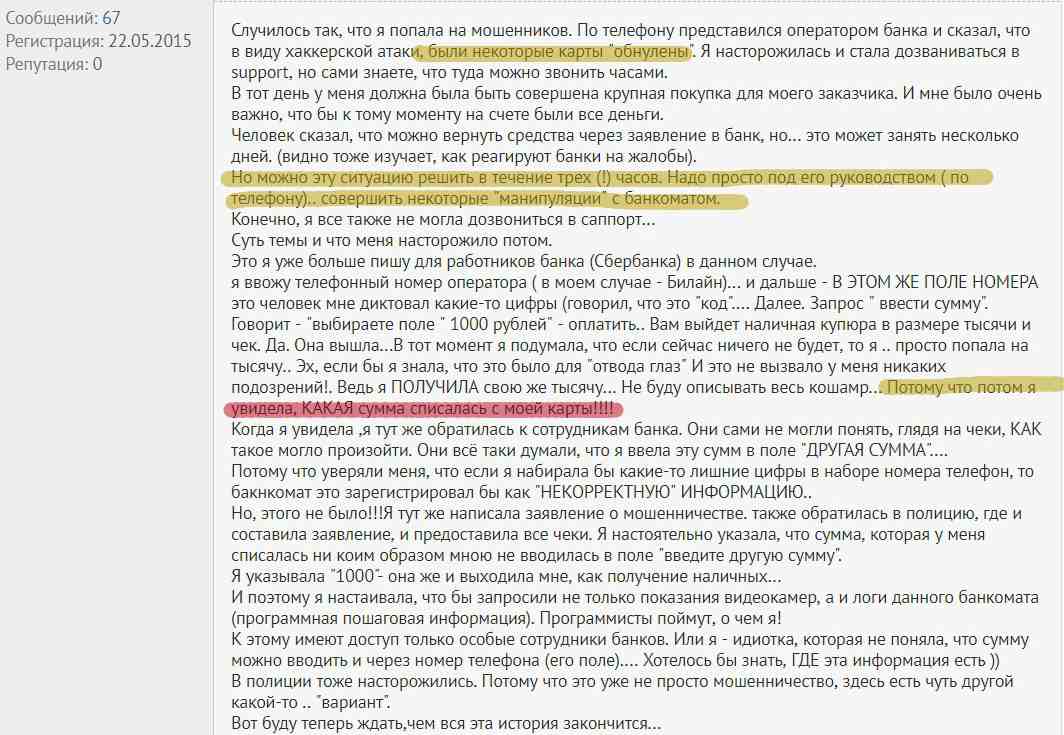
How to prevent fraud through mobile banking
The basis for the safe use of plastic cards, as well as mobile banking, is attentiveness and prudence. There is no need to use an ATM unless you are sure that it is well lit and can be viewed from different angles by external surveillance cameras. No need to enter your mobile banking password in the middle of a shopping mall. Do not open suspicious SMS and emails. And especially - you shouldn’t believe every teleophonic well-wisher.
We are responding to people who had money withdrawn through Sberbank’s mobile bank. The following steps will help you avoid trouble:
- order an additional card and use it for payments in shops, restaurants, gas stations - such a card should always have a small amount of money, limited limits;
- set a daily withdrawal limit for all cards, regardless of how often you use them;
- Always choose new generation cards with additional security measures - chip, photo.
Ways to protect yourself from phishing:
- purchasing licensed applications,
- downloading free programs from official sites,
- control of the movement of money in the account.
Important: worry about safety in advance. For example, install an antivirus on your smartphone, and specify duplication of messages by email in the settings of your personal bank account.
Real reviews from bank clients indicate that you can avoid vishing if you do not open messages received from unfamiliar numbers. We advise you to periodically check the list of programs installed on your phone.
Sberbank offers a subscription to the Secure Code service. This is a special code that the system generates for a specific plastic card.
Useful links on the topic “What to do if they withdraw money from your phone”
- Let's talk - virtual telecom operator of Sberbank
- Directory of USSD commands Beeline Megafon MTS Tele2 Yota
- How to deal with advertising calls and calls to your home and mobile phone
- How to deal with SMS spam
- How to write a complaint (general recommendations)
- SMS “divorce” on websites
- The European Commission will relieve subscribers from huge roaming bills
- Mobile scammers: how to protect yourself
- 23 mobile fraud schemes
- SMS scammers have reached bank cards
- How to protect your mobile phone from theft
- How to get money back if your mobile phone is broken
- Tricks of mobile operators
- How to win a lawsuit against a mobile phone store
- Mobile and bailiffs: history of the dispute
- For the first time, a mobile operator was fined for someone else's paid SMS
- Blacklist of mobile phone scammers
- Sample claim for exchange (return) of a phone
How to get back lost money
Success depends on the speed of contacting technical support and the availability of evidence. We propose the following algorithm of actions:
- urgently call the hotline number to block the movement of money in the account;
- come to a bank branch, report the incident, fill out a standard application;
- provide evidence of your innocence, attend meetings with security department employees;
- write a statement to the police, regularly inquire about the results of the investigation.
The user has the right to demand that the case be considered in court if the bank decides not to return the funds or law enforcement agencies fail to act.
That's all.











